Sunday, January 21, 2007
Hack Google Talk
Unfortunately, Google Talk doesn’t connect with other instant messaging networks, such as AOL Instant Messenger or Yahoo! Messenger; with Google Talk, you’re pretty much limited to IM’ing with other Google Talk users. Unless, that is, you know the trick.
How the Hack Works
Google Talk is built on the Jabber protocol, which allows for interoperability between compatible IM services. And if you hack Google Talk to connect to a Jabber server, you can then connect Google Talk to the AIM, ICQ, MSN Messenger, and Yahoo! Messenger networks.
What you have to do is connect Google Talk to a Jabber server, and from there use a specialized transport to connect to your IM network of choice. Essentially, the connection goes from Google Talk, through the Jabber server, through a transport for the selected IM network, and then to that that IM network. When it works, it’s relatively seamless; you can talk to friends from virtually any IM network through the Google Talk client.
Of course, to connect to another IM network in this manner, you must already be a subscriber to that network. During the connection process, you’ll be prompted to enter your username and password for any IM service you try to connect to. You’ll also need to have Google Talk installed and running on your system, and have a valid Gmail address (which you need to use Google Talk in the first place).
Making the Hack
Here’s how to connect Google Talk to any competing instant messaging network. It involves downloading, installing, and configuring a separate Jabber instant messaging client, in addition to the Google Talk client.Begin by going to the Psi website. Psi distributes a free Jabber client; follow the onscreen instructions to download and install the Psi client on your computer.
Once you have the Psi client installed, launch it. When it’s up and running, click the Psi button in the lower-left corner and select Account Setup.
When the Jabber Accounts dialog box appears, click the Add button. In the Name: field, type Google Talk, then make sure the Register New Account option is not checked. When you’re done, click the Add button in this dialog box.The Account Properties dialog box should now appear. Select the Account tab, then enter your full Gmail email address into the Jabber ID field. Next, select the Connection tab. Check all the options on this tab, then enter talk.google.com into the Host field. Click the Save button when done.
Back in the main Psi window, click the Psi button again and select Service Discovery > Google Talk. When the Service Discovery dialog box appears, enter the address of any public Jabber server into the Address box and then press Enter. Where do you find the Jabber server address? Easy; you can find a complete list of public Jabber servers on the Jabber website. Know, however, that not all Jabber servers offer transports for all instant messaging networks, so you may have to try more than one server to find one that offers the IM transport you want.
Once you connect the Psi client to the selected Jabber server, you should see a list of available IM transports (among other things) available from this server.
Click the transport for the IM network you want to connect to. Wait a few seconds for Psi to gather the appropriate data for the selected transport, then right-click on the transport and select the Register option.When the Registration dialog box appears, enter your username and password for that IM network then click the Register button.
Psi will now connect to the selected IM network and retrieve your existing contacts. As Psi adds your IM contacts, you’ll probably receive a series of system messages asking you to okay the addition of each contact. Click the Add/Auth button to authorize each contact. Then, once your contacts have been retrieved, exit Psi.
Using Google Talk with Other IM Networks
The next time you launch Google Talk, all your contacts from the selected IM service should be listed in your Google Talk Friends list. When you click any of those IM network’s contacts from within Google Talk, you automatically connect to that network and can IM to your heart’s content.
It’s a bit awkward, but this hack effectively turns Google Talk into a universal instant messaging client. Neat!
Spam free GMAIL
It is a very simple task to provide an alias of your gmail id. Whenever you sign up on the internet on some site that you think may not be safe(or a site which might send you spam),all you have to do is give out the email address as
username+insertanythingyouwanthere@gmail.com
For example if your email id is james@gmail.com,you can provide james+21@gmail.com or james+test@gmail.com .You can put anything after the + and all email sent will still go to your gmail account.
In the event that you did give your email to a spammer and you start receiving spam, don't worry! Just create a filter, and make everything that is sent to username+whateveryouputhere@gmail.com go to the trash. This way all the spam that you might get will automatically be deleted.Did you find it useful?Feel free to comment.
Saturday, January 20, 2007
Dual boot Windows Vista Beta and XP

Now, Microsoft says only developers, testers and those "experienced in PC troubleshooting" should install this on a spare machine. But I'm young, stupid and reckless so I installed Vista on my main PC which is the only machine I have souped up enough to handle the Vistage. I didn't want to let go of XP, though, in case everything went to hell. Thankfully all turned out well: I now have a single dual-boot PC that can run either Vista or XP.
Free partitioning utilities (like the one on the XP setup disk) delete all the data on the disk when they create new partitions. That's not very convenient. Norton's commercial product called PartitionMagic, which you can purchase at Amazon for $43 (after rebate), however, can create a new partition out of free space on your C: drive without killing the rest of the files. That's what you want. UPDATE: Astute reader Barron says that the GParted Live CD also works and it's free. Thanks Barron!

Now, once Windows XP is fully booted up and you can see your new 20GB drive, pop in the Vista DVD and run the install from there. Choose your newly created V: drive as the installation location, and let 'er rip. Vista will spend lots of time copying files and restarting your machine. All goes well in installation-ville, and you'll set up your first administrative Vista user and go from there.
Now, once you restart your computer, you'll get a choice to boot into XP or Vista.

Wednesday, January 17, 2007
Top Yahoo! messenger Widgets

Note: All reviewed widgets can be installed for your Yahoo Messenger if the following requirements are met:1. Yahoo Messenger v. 8+2. You are signed in to the application3. You click the download link ;)
The most popular of them all, is
- Yahoo! Avatars Space. You can hang out in style with your virtual friends. Launch this plug-in to open a cool Avatars-only environment that you can customize by changing the background, furniture and artwork. Change your Avatar’s mood on the fly and use the DECORATE command in your IM conversation to spice up the room with pictures from Yahoo! Image Search.
- YEmotePLUS plugin, unlike its predecessor was re-written from scratch to include all the features users requested and some additional. For those that want more then the simple smiley menu of Yahoo, YEmotePLUS gives you access to ALL the secret and hidden Emoticons / Smileys quickly, and they even animate on mouse-over.
- Pando and it comes in helping those who need to share large files and even folders, at a time, with their contacts list. Do I have to say more?
- NewsGator’s editors search through hundreds of thousands RSS feeds to find you the coolest video and audio podcasts and the most interesting stories from around the web, so you can enjoy them right within your Yahoo! Messenger. You can even personalize your experience by creating a free NewsGator online account, selecting your own feeds, and reading your stories from within the NewsGator plug-in.
- Eazibo. The best way to interactively and instantly make flowcharts or diagrams, share photos and make annotations with your friends online while talking on VOIP. It’s called “Instant Graphics”. Futuristic, but real today.
These being said, I’m going to let you explore the widget universe of Yahoo Messenger, as soon that I let you know we’re looking forward to hear your suggestions, opinions and comments.
Password Generator
This is an idea I’ve been rolling around in my head for some time. Now that I have a blog, I can finally share it with you:
For years, system administrators and savvy users have needed to create long passwords to thwart password guessing attacks. However, those passwords are complicated and hard to remember. Is there a way to create strong, easy to remember passwords that are impervious to most attacks?
Yes, thanks to something I call the compound password. It’s very simple, but also incredibly powerful. Essentially, the compound password is a juxtaposition of two simple words, with their letters alternating.
For example, dcoagt is a compound password.
Can you see the two words in there? How about now: dcoagt .
The two words in the compound password are “cat” and “dog”. To generate the password, “cat” is “inserted” into “dog”. But what of memorability? To the unenlightened, this looks like randomly generated, hard to remember ASCII text. But, remember, this is nothing more than the juxtaposition of two words. A simple entry trick means that all you will need to remember is your two words any time you need to type in that password.
Here’s how:
(The represents the flashing entry thingie doh, cursor that shows where you are in any text entry field, and should not be typed in):
- Enter the first keyword cat
- Hold down the left arrow to move to the beginning of the line cat
- Enter the first letter of the second keyword and press the right arrow once dcat
- Enter the next letter of the second keyword and press the right arrow once dcoat
- Repeat step 4 until the second keyword is fully entered. dcoagt
That’s it! You now have yourself an impregnable compound password! Now a look at some of the most common password grabbing techniques, and how compound passwords thwart all of them:
Brute Force The most common reason administrators urge users to choose long passwords with letters and numbers is to thwart brute force attacks, which try every possible combination of letters and numbers to guess the password. As the length of a password increases, the computing power required to guess every combination increases exponentially. Sure, dcoagt may be easy to bruteforce, but what about bguesohrgew (georgew bush)?
Dictionary A variation on brute force is guessing passwords from a predefined dictionary/wordlist, often appending single or double digit numbers to the end. This improvement on brute force still can’t guess compound passwords though, as they are not found in any dicitonary.Guessing Same as dictionary. If someone randomy decides to try dcoagt, they should skip hacking and go straight for the Randi Prize .
With a couple more tricks, even more advanced password grabbers can be foiled.
Keyloggers Malicious trojans and keyloggers have the capacity to record every keystroke you make at your computer. However, they do not record mouse clicks. If you are afraid of keyloggers, simple replace each keyboard arrow press with a mouse click- enter your first keyword, click at the beginning of the entry field, etc. The keylogger will only capture the keys you press which will look like this: catdog , not even close to your actual password. Great for public computers.
Shoulder Surfing Shoulder surfing is simply when an attacker stands behind you, watching the keys you press on your keyboard. However, 99% of the time, he will not observe the keyboard arrows you are pressing. Simply put one hand over the arrows and covertly press them as needed while you enter the password with your other hand.
Compound passwords are not a magical solution to everything. They will not protect from phishing attacks or database compromises. But they are an easy way to generate strong, memorable passwords.
People! dcoagt is just an example! I picked three letter words to combine for ease of demonstration! A real password would have longer words and special characters thrown in there, and would be more like edfifgegc!t (digg! effect). Better?
Sunday, January 14, 2007
Hidden XP tricks
Open an image and select the magnifying glass icon. Left-Click exactly on the line below the 8x.
Hidden Command Line SwitchInstructions -
Go to "Start", "Run" and Type defrag c: -b to defragment the Boot and Application Prefetch information.
Support ToolsSecret -
Over 100 Windows XP Support Utilities are on the install CDInstructions for Pre-SP2 users - If you do not have SP2 installed, put the original Windows XP CD in the CD-ROM Drive, run the D:\Support\Tools\setup.exe file.
Music from the InstallerInstructions -
Browse to C:\Windows\system32\oobe\images\title.wma and play.
Device Manager-Hidden DevicesInstructions -
Go to the "Control Panel", "System" icon, "Hardware" tab and select "Device Manager". Select "View" and Show hidden devices.
Secret - Phantom DevicesInstructions -
Go to "Start", "Programs", "Accessories" and select "Command Prompt". At the command prompt, type "set devmgr_show_nonpresent_devices=1" and press Enter. At the command prompt, type "start devmgmt.msc" and press Enter. Select "View" and Show hidden devices. You can see devices that are not connected to the computer. - Source
Notes -
When you close the command prompt window, Windows clears the "devmgr_show_nonpresent_devices=1" variable that you set and prevents phantom devices from being displayed when you select "Show hidden devices".
Add/RemoveSecret -
Hidden Uninstall OptionsInstructions - Warning: Proceed at your own risk! Browse to C:\Windows\inf\ and make a backup copy of sysoc.inf. Then open the original file C:\Windows\inf\sysoc.inf in notepad. Go to "Edit" and select "Replace". In "Find what:" type ,hide and in "Replace with:" type , then select "Replace All", save and close the file. Go to the "Control Panel", "Add/Remove", select "Add/Remove Windows Components". You will now see many more Windows components to uninstall. Do not remove anything with no label or that you do not recognize or fully understand what it does
Friday, January 12, 2007
VISTA messenger from Yahoo!
 Yahoo! messenger
Yahoo! messenger for VISTA
Yahoo! is building a new version of its Messenger communications service specifically for the Windows Vista operating system. Yahoo! Messenger for Vista will be previewed Monday at the Consumer Electronics Show in Las Vegas and will be launched in public beta during the second quarter. It offers the ability to resize the contacts window and to start a chat without opening a chat window, easy access to a color wheel to change the background color, and the ability to make photos full-screen size when sharing them. Users can also combine multiple chat sessions into one window with multiple tabs and can drag and drop a contact onto the desktop for separate viewing.

Another new feature is the automatic creation of contact groups based on Yahoo! network affinity groups of which users may be members. For instance, a user who is in the Yahoo! Fantasy Football group can see other group contacts in the Messenger window or separate them out into a new window.

Yahoo! have compiled a nice video demo for Yahoo! Messenger for Vista, check it out
Yahoo! Messenger for Vista also leverages the desktop search in Vista to let the user search for photos stored on the computer, and it includes new animated emoticons.
Features:
- Instant message, voice, webcam video, and more
- Use the integrated Yahoo! Messenger Sidebar gadget to keep up with the friends that matter most
- Also add Windows Live™ Messenger friends to your contact list to see when they’re online and IM them
- Keep conversations organized by dragging and dropping them into one tabbed window
Brand new emoticons, program icons and alert sounds - Instantly change the look and feel of your Yahoo! Messenger interface
- Automatic groups are created in your contact list based on your Yahoo! interests (i.e. Yahoo! Sports Fantasy Football league)
KEEP TRACK OF THIS PAGE 2 GET THE BETA DOWNLOAD LINK SOON
Desi Mail for Desi People
One fine day when I checked my Rediffmail free email account, I just couldn’t believe my eyes 00...Sitting right there above the login form fields was a small message that mentioned a 1GB space for the email account!!! Rediffmail also has a paid version for their email service, which I guess has had a reasonable amount of success, so I thought that this 1GB is a good idea to gather more paid members. However, to my utter surprise when I entered by INBOX and on a hunch checked the "Storage Space" I found that this 1GB space is for the free accounts. I almost fell off my chair!!!
Rediff and Rediffmail
For those who don’t know about Rediffmail, it has been one of the premier web email providers in India. Their portal (www.rediff.com) is also very popular – at least I use its cricket section whenever I need to check scores. Rediff was one of the first to launch a portal of stature in India. Riding the Internet wave (to use a cliché), several other companies made their online presence. There was Indiainfo.com, which had advertised in all forms all over the country and is now forgotten by most of us! Indiatimes.com was a portal launched by the Times of India newspaper group. I guess, it has also been a success because it has a very good offline medium to advertise – the Time of India newspaper… And there was Indya (www.indya.com). All these portals offered free email accounts.
A few years back Rediffmail came up with a brilliant idea. It started to advertise its free email account service – their punch line was Lightning fast email and it indeed was! At that time, net users in India used popular email services like Hotmail, Yahoo!, Snap etc. and most of us accessed the Internet with dial-up connections which were very slow. Accessing the INBOX at Hotmail or Yahoo! was so frustrating as it used to take so much time. I guess Rediff would have done a consumer survey and received a feedback that people needed to access email over quick servers. With their lightning fast email servers Rediffmail gave what everyone in India wanted – fast access to online email.
The very idea of advertising a free email service and spending money to upgrade it was something that other portals had not thought about. Rediffmail’s competition too advertised their services but the ads mentioned different services offered by the portal and did not put emphasis on one particular service.The Lightning fast Rediffmail gained a loyal following.This was followed by the email over mobile phone service from Rediffmail. Users could access the Rediffmail INBOX via their cell phones.
Nowadays, since, most net surfers in India either use cable or DSL (or sit at CyberCafes which use either of these services), accessing the Internet over fast connections is no longer a problem. So Rediffmail comes up with another beauty – offering free 1GB email account. Obviously, this step has been prompted by the release of Gmail, but the fact that an Indian company has taken this step is something that all Indians should be proud of!
Testing the Rediffmail 1GB
I sent four emails to my Rediffmail account with fairly large attachmentsfrom my friends computer. Using DSL, I was able to download these emails back to my computer in seconds - 12.9MB, 1.1MB, 4.4MB and 7.4Mbtook 119, 10, 32 and 72 seconds respectively. So Rediffmail is not only lightning fast it also provides a huge storage space.
Tuesday, January 09, 2007
HOW TO HACK AOL®, YAHOO® AND HOTMAIL®
I get numerous calls from people who want to recover AOL®, Yahoo® or Hotmail® or other online and email passwords. I do not do this type of work. Many of these people claim that they have lost their passwords because they have been hacked and now need to get their password back. As I have reviewed information on the web, I found very little real information about the actual techniques that could be used to hack these services. So I decided to pull together a detailed explanation. What follows is a detailed explanation of the methodologies involved. I do not condone any illegal activity and I clearly mention in this article techniques that are illegal. Sometimes these methods are known as "Phishing."
THE HOAX
Let's dispose of one technique that is absolutely a hoax (meaning a fraud: something intended to deceive; deliberate trickery intended to gain an advantage.) If you see a newsgroup post or web page with something like the following, it is a hoax and will not work.
: : : (([[THIS REALLY WORKS ]])) : : :
(1) send an E-mail to passwordrecovery@yourdomainhere.com
(2) In the subject box type the screenname of the person whose password you wish to steal
(3) In the message box type the following: /cgi-bin/start?v703&login.USER=passmachine&class=supervisor&f={your aol password}&f=27586&javascript=ACTIVE&rsa
(4) Send the e-mail with priority set to "high" (red ! in some mailprograms)
(5) wait 2-3 minutes and check your mail
(6) Read the message.-Where YOUR password was typed before, NOW, the password of the screenname in the code string is there!!!
Why does this work? It´s a special decryption-server that AOL-employees can use to decrypt passwords.The aolbackdoor account is a bot that reads your authentification from the message body and identifiying you as a valid AOL Staff-member, you will get the password mailed back to you. The trick is that this Bot´s script seems to be a little bit buggy and it automatically recogises you as an supervisor (AOL-Staff member), even if you use a normal AOL account. This means, that EVERYONE having a valid AOL account can hack as many other accounts as he wants.
This is just a scam to steal your password and may explain some of the calls I get from people saying they were hacked. Never give your password to anyone. No legitimate web service or customer service representative will ask for it or need it. There is no magic email address or series of commands that will reveal the passwords of users.
LOCALLY STORED PASSWORDS
Most browsers, including Internet Explorer® and Netscape®, the AOL® client, and Windows® Dial-Up Connections allow you the option to store passwords. These passwords are stored on the local machine and (depending upon where and how it is stored) there is usually a method of recovering these passwords. Storing any password locally is insecure and may allow the password to be recovered by anyone who has access to the local machine. While I am not currently aware of any program to recover locally stored AOL® passwords, I do not recommend that these are secure. Software does exist that can recover most of the other types of locally stored passwords.
TROJAN
A Trojan is a program that is sent to a user that allows an attacker to control functions of the target computer, recover information from the target or to delete or damage files on the target. The name Trojan is given because the program will usually come attached to some other program or file that entices you to run it. There are a wide variety of Trojans any number of which can be programmed to capture passwords as they are typed and to email or transmit them to a third party. To protect yourself against Trojans, you should never execute or download software or files that are not from a trusted source. It is critical that anyone working on internet use a virus protection program (which should catch most Trojans.) Note that since a Trojan requires the password to be typed or stored in order to be recovered, this is not an effective way to recover your own password. It could explain, however, how someone could lose their password to a hacker. Sending someone a Trojan program is certainly illegal and I do not recommend or condone this activity. A Trojan is unlikely to be effective in recovering a particular account password since it requires the target to install it. However, hackers will often bulk mail Trojans to thousands of people in the hope that a small percentage will get caught. Legitimate account holders who may have been caught by a Trojan and can authenticate themselves should contact their service provider to have their account passwords reset.
KEYLOGGER
A keylogger is a program or piece of hardware that records all keyboard keystrokes to an encrypted file which can then be read later. Based on the order of the keystrokes, it is usually easy to identify the password(s) from the file later. Like the Trojan, this also requires that someone actually type the password. Keyloggers come in two types: hardware and software. A hardware keylogger can be fitted between the keyboard cable and the computer and can be activated with a few keystrokes. It is then left in place until after the password that you are looking to recover is typed. Later it is removed and the file of keystrokes is examined for the password. A hardware keylogger is undectable by anti-virus software. A software keylogger is installed on a system and effectively has the same function, however, it is a little bit more complex to use since it must be installed to run stealthily to be effective. A keylogger could be used to steal a password from someone who is using an office computer or sharing a computer. It is possible that installing and using such a device or piece of software could be illegal depending upon whether the target has a presumption of privacy when using the computer on which the keylogger is installed. SNIFFING
If two people do not share the same computer, but do share the same network, it may be possible for one to sniff the others' packets as they sign-on. The traffic between your computer and the internet site you are accessing may be able to be recorded and decrypted or "played-back." This is not a simple attack to execute, but is possible if two people are close to one another and share a hub. Again, this is likely to be illegal and I do not condone this activity.
BRUTE-FORCE ATTACK
Many people want to find software to perform a brute-force attack. This is really impractical. It would take hundreds of thousands of years to attempt any kind of reasonable brute-force attack on AOL®, Yahoo® or Hotmail® and this would expand exponentially if the password is longer than the minimum length. Using multiple computers or multiple sessions could reduce this to merely thousands of years. This is highly illegal since these services own the servers on which an account is hosted. Even if you are hacking your own account, you don't own the servers and the service is going to monitor and log this activity. It is extremely unlikely that you could recover a password in this way, but it is extremely likely that you'd be arrested and prosecuted for doing this.
Thursday, January 04, 2007
Beta Mail War
Yahoo! Mail beta :
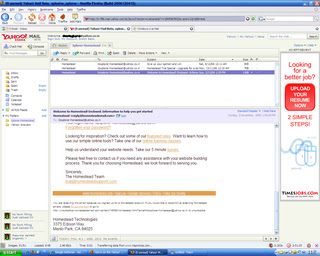 The original Yahoo Mail web-based client is now looking somewhat dated compared to offer newer offerings. Enter the new beta service from Yahoo, which is a giant step-up from the previous old, clunky interface. The new beta is fully Ajax‘d up and is easily the most immediately impressive out of the three products being examined here. The interface is very clear, easy to use, very quick to respond and is more reminiscent of a fully fledged desktop client than a browser-based utility. Its definitely a contender for an idealistic 'Web 2.0' product.
The original Yahoo Mail web-based client is now looking somewhat dated compared to offer newer offerings. Enter the new beta service from Yahoo, which is a giant step-up from the previous old, clunky interface. The new beta is fully Ajax‘d up and is easily the most immediately impressive out of the three products being examined here. The interface is very clear, easy to use, very quick to respond and is more reminiscent of a fully fledged desktop client than a browser-based utility. Its definitely a contender for an idealistic 'Web 2.0' product.A clearly defined left-hand-side navigation pane, and a multi-tab viewing window that allows, for example, your inbox coupled with a preview pane or a newly invoked tab displaying an individual email, is easily one of the best interfaces for web-mail I’ve used to date. These sort of advanced Ajax features could be slow and unresponsive in a poorly implemented design – but Yahoo has ensured they’re almost as quick as a standard desktop application, with the added portability of a web-based client. It works perfectly with Firefox and now wth Opera too. All of these positive attributes add-up to ensure Yahoo is on to a winner with their updated mail service.
INQ RATING :9/10
Excellent 'Web 2.0' functionality, competently able to replace your desktop mail client on Firefox or Internet Explorer.
Gmail beta :
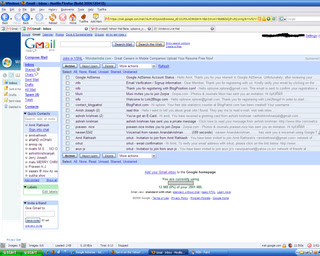 Gmail caused quite a storm on its release, one gigabyte of storage (now over 2gb) shook up the online email market somewhat, and a slew of competitors quickly ramped up their offerings to stop the speeding up-take of Google’s brand new in-beta product. This coupled with their invite-only marketing ruse, which seemed to invoke furore on the internet, with everyone grabbling for invites and even purchasing them via eBay in an attempt to get a ‘trendy’ .gmail.com address. Despite the over-the-top hype, Google’s offering is a very accomplished first stab at an online email service provision. Fully Ajax-enabled, the interface is very simple, quick and simple to use. Instead of folders ‘Labels’ are used, allowing the quick viewing of custom-labelled emails and items, through the label sub-menu. Removing labelled items from your main inbox to allow them only to appear in the labelled view, is only realisable by choosing to label, then archive an email – a slightly odd way of doing things. The archive feature is also useful – removing those emails from your inbox you’d rather not see day-to-day, but keeping them safe and searchable within the vast storage Gmail offers.
Gmail caused quite a storm on its release, one gigabyte of storage (now over 2gb) shook up the online email market somewhat, and a slew of competitors quickly ramped up their offerings to stop the speeding up-take of Google’s brand new in-beta product. This coupled with their invite-only marketing ruse, which seemed to invoke furore on the internet, with everyone grabbling for invites and even purchasing them via eBay in an attempt to get a ‘trendy’ .gmail.com address. Despite the over-the-top hype, Google’s offering is a very accomplished first stab at an online email service provision. Fully Ajax-enabled, the interface is very simple, quick and simple to use. Instead of folders ‘Labels’ are used, allowing the quick viewing of custom-labelled emails and items, through the label sub-menu. Removing labelled items from your main inbox to allow them only to appear in the labelled view, is only realisable by choosing to label, then archive an email – a slightly odd way of doing things. The archive feature is also useful – removing those emails from your inbox you’d rather not see day-to-day, but keeping them safe and searchable within the vast storage Gmail offers.As you may know, Google have released their own chat client; Google Talk, which provides VOIP services as well as standard text-based instant messaging. Interestingly, once logged in, the Gmail homepage provides you with a brilliantly realised web-based chat client that can provide similar IM functionality to that of Google Talk – with the same contacts and contact information. This is easily turned off at the bottom of the page if people are pestering you every time you check your email. Its an incredibly useful implementation, allowing IM anywhere you have web access without having to install a client and mess around with the host’s ports. Its certainly the best webpage-embedded IM solution I’ve seen thus far.
Some of the more ‘advanced’ features are usually hidden in an attempt to make the service immediately easier to use, these can quickly be found, but some users may prefer than an option to keep them permanently viewable was present.
The only worrying thing about a Google product offering, is how they’ll use your personal data. Already adverts appear that are being served from keywords in your emails. If you can live with Google’s relentless stride towards owning all information, everywhere, and want a simple web-based email client that doesn’t necessarily mimic a desktop-equivalent, Gmail may be for you.
INQ RATING: 8/10
A very quick, responsive service with a simple interface, bellying a more complex, useful online email client.
Windows Live Mail beta :
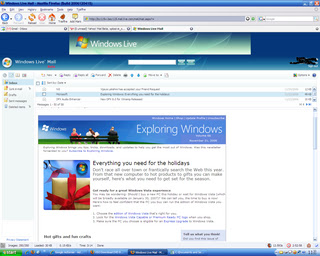
A recent addition to Microsoft’s ‘Live’ initiative, the new Windows Live Mail which seems to be an attempt at replacing Microsoft’s Hotmail offering, is the last of the three services here, to have entered beta testing. Hotmail is already pretty clunky and painful to use compared to a decently Ajax’d equivalent and I was looking forward to banishing this interface to a distant memory. However, as an alleged ‘beta’ product I was shocked at the numerous bugs, errors, and not-so-trivial problems I had when attempting to use the product over several months. While the other reviews here centre on the quality of offerings from Microsoft’s competitors, this will inevitably centre on the poorness of the product from the Hotmail team.
Spam is still inherent within the Hotmail service, despite Microsoft’s sabre-rattling’s about spam. I get at least 10-20 spam’s a day that aren’t caught by Microsoft’s spam filter out of about 40 total spams. Compared to Yahoo’s (around 5-10 not caught from 200) and Gmail (1 from 50) statistically Live’s spam filter is seemingly the least effective. It also seems to catch a lot of ‘real’ emails – something that the other two services hardly ever seem to do. These aren’t hard statistics though, only a rough guide from an end-user’s point of view.
The interface is very simple, with a left hand navigation pane, a list of your email in the main pain, and a preview pane, analogous to the usual Outlook Express view. The Live mail team may wish to look at Yahoo’s mail for a much better interface look, feel and style.
The Ajax-based requests seem to be slower than either of the other two sites. Hotmail has always been very sluggish and prone to service problems and this seems to be compounded when moving to an Ajax-esque front-end – displays similar to ‘Your request is being sent’ seem to appear for long periods, sometimes without ever disappearing, forcing a new request by the user to be performed. Multi-selecting items to send them to a folder, or select them as spam, produces a ‘We were not able to complete your request’ around fifty per-cent of the time – albeit the function has usually been performed.
Originally the service didn’t support Firefox - a later build of the product which went live, attempted to fix this, but was subsequently pulled due to unknown problems with the rest of the service. Since its reinsertion I’ve not been able to view my inbox in either client, albeit I hear that on other people’s designated servers it seems to be fine. Thus other the last month, or so, I’ve had to resort to the ‘Classic’ view which forces the Live mail service to use a more Hotmail-esque display, without the many Ajax-based additions. The enhanced Live Mail service simply won’t load on any machine I try it on – Internet Explorer returns a JavaScript error and no inbox, Firefox produces an error page asking you to report the error to Microsoft – the link to perform the feedback is broken.
INQ RATING 2/10
Microsoft must try harder.
Conclusions:
Those wishing for a full-blown desktop client replacement need not look further than Yahoo! Mail. Impressively designed and executed, I can find little fault with Yahoo’s product. Those wishing for a slightly less full-blown desktop-orientated design approach should certainly check out Google’s Gmail (or Googlemail as it’s known). This provides very quick email authoring, searching and browsing, coupled with a rather excellent web-based chat client – provided you are happy with Google’s continuing encroaches into your private data.
I cannot recommend Hotmail in any way. Spam is still a huge issue that Microsoft cannot seem to cope with, especially when coupled with their Hotmail/Live service. Even though the product is said to be beta, it seems more alpha-build quality and should never have been released to the public in this form. This is another rushed product to counter Google et al, that doesn’t come near to the quality of other Microsoft Live beta services such as ‘Windows Live Local’, let alone competitors rival products. µ L’Inqs